Elizabeth G. Boulton, PhD
https://doi.org/10.21140/mcuj.20221301005
PRINTER FRIENDLY PDF
EPUB
AUDIOBOOK
Abstract: A transdisciplinary research project investigated the idea of framing climate and environmental change (CEC) as a new type of threat: a hyperthreat. Traditional military analytical methods were used to assess the hyperthreat and its context and develop ideas about how an adequate response could be conceived. This approach contrasts to prior literature and longstanding geopolitical discourse that identify the risks of taking a securitization approach. Instead, the author argues that it is now riskier not to consider CEC within a mainstream geopolitical and nation-state security strategy. When the hyperthreat of CEC is centered as the main threat to be contained, and its relationship to other threats is analyzed, startling new pathways to stability emerge. The research developed a new theoretical approach called “entangled security” to develop an initial new “grand narrative” and “grand strategy” (PLAN E). This article offers a vision of how military theory can be reimagined to support new policy directions and security priorities.
Keywords: PLAN E, hyperthreat, entangled security, climate change, hyperobject, military strategy, climate emergency, mobilization, transdisciplinary
Introduction
During the 2019–20 Australian bushfire catastrophe, to effectively convey the magnitude of what they were experiencing, public discourse suddenly became littered with warlike terms and analogies. People spoke of the “next bushfire assault,” “ember attacks,” and doing “whatever it takes to defend the town.” Navy ships evacuated citizens, and a climate scientist argued that “failing to adequately plan for the known threat of climate change
. . . should now be considered . . . an act of treason.”1
Similar language is seen in other global climate extremes and emergencies. At such times, the author proposes, threat-like language is used by people not because they wish to securitize the problem, but rather because it helps them to articulate and describe their experiences. Similarly, in geopolitical discourse, describing climate and environmental change (CEC) as a “threat” is not novel—it is pervasive. In the Pacific Island Forum’s “Boe Declaration on Regional Security,” climate change is described as the “single greatest threat,” while at the United Nations (UN) Security Council, Sir David Attenborough proposed CEC presented “threats to security of a new and unprecedented kind.”2 Meanwhile, in the United States the Joseph R. Biden Jr. and Kamala Harris administration has put “the climate crisis at the center of US foreign policy and national security.”3 To be elaborated on below, in academia, climate and environmental change has prompted widespread revision of how security is understood.
This article reports on a research project that centered around this question: If CEC is framed as a new type of threat—existential, catastrophic, or an emergency—then could extant military threat analysis methods be applied to the problem to inform civil response? The focus of the exploration was on deep frames, or the theoretical conception of threat, with traditional threat analysis methods used in a light manner. The term deep frames comes from neuro and cognitive science research; it refers to complex networks of neuron pathways that hold a person’s guiding worldview, identity, values, and influence decision making—mostly at the subconscious level. 4 As cognitive scientist George Lakoff writes:
Real reason is: mostly unconscious (98%); requires emotion; uses the “logic” of frames, metaphors, and narratives; is physical (in brain circuitry); and varies considerably, as frames vary.5
With this Journal of Advanced Military Studies issue exploring military contributions to disaster response, the following article proposes that contributions could also be intellectual: military theory can be applied to the planetary-level disaster of climate as well as to ecological crisis.
To introduce the research, the article will provide an overview of the development of the hyperthreat concept and reflect on the strategic rationale for threat framing. Next, prior climate-security literature will be reviewed, with an explanation of how this research departs from previous work and seeks to address gaps in knowledge. The article will then describe the methodology used for the research project. The bulk of the article then turns to discussing the new research insights and conclusions reached. The outcome of the research is a prototype grand strategy, called PLAN E, which has also been published separately in Expeditions with MCUP.6 Because this research is transdisciplinary and uses technical terms from a range of disciplines and involves the creation of new terms, a glossary is provided to aid comprehension across specialties.
Ecophilosopher Timothy Morton and Climate as a Hyperobject
Drawing on Clausewitzian approaches, the first phase of the research focused on developing an understanding of the nature and form of the climate and environmental threat and determining its underpinning sources of power. Pivotal to this exploration was ecophilosopher Timothy Morton’s concept of global warming as a “hyperobject.” Morton’s work was notable for its abrupt departure from the norms of climate discourse, whereby instead of presenting humanity with long lists of statistics, Morton materializes global warming. The hyperobject, Morton argues, displaces humans as the most powerful actor on Earth and renders humanity now weak, lame, and vulnerable.7 It is a complex notion and new philosophical vision; however, in simple terms, a hyperobject is a gigantic new “thing” that humanity has not encountered before; it moves like fog, is diffused through everyday life, and is beyond human sensory and perceptive capacities. The hyperobject’s presence disrupts and displaces humanity’s sense of existential identity:
Yet what has happened so far during the epoch of the Anthropocene has been the gradual realization by humans that they are not running the show, at the very moment of their most powerful technical mastery on a planetary scale. Humans are not the conductors of meaning, not the pianists of the real.8
Focusing on a New Form of Violence—the Hyperthreat Concept
Morton’s hyperobject theory was then placed into a security context to develop the related concept of a hyperthreat:
The hyperthreat has warlike destructive capabilities that are so diffuse that it is hard to see the enormity of the destruction coherently nor who is responsible for its hostile actions. It defies existing human thought and institutional constructs.9
In contrast to the more commonly used crisification framings like “climate crisis” or “ecological emergency”—which highlight urgency—the hyperthreat frame spotlights the harm, killing, violence, destruction, and loss of freedoms imposed by unraveling ecological and climate systems.10 This approach was also informed by and extended Rob Nixon’s concept of slow violence, whereby destruction of the environment (through impacting people’s livelihoods, health, food, or water supply) can inflict harm and kill slowly.11 Another influence on the hyperthreat concept were ecotheological approaches, which focus on “creation care” and question how the “do not kill” ethic might apply in the context of an ecological crisis.12 All of this deliberation led to the conclusion, embedded within the hyperthreat concept, that security theorists need to revise their understandings of culpability or hostile intent to cause harm.
In comparison to Morton’s hyperobject frame, the hyperthreat notion includes general environmental destruction and degradation, not just global warming. Also, the hyperthreat notion dares to reclaim some human agency. Concepts from military studies, like the importance of moral forces and the capacity to mobilize around overwhelming threat, inform the development of the hyperthreat notion. For example, applying just war theory to the hyperthreat led to the argument that there are three good reasons for humans to mobilize against the hyperthreat: one, the risk of general destruction; two, the loss of autonomy and freedom; and three, due to survival imperatives.13
Application of a Hyperthreat Framing
Once a concept of threat had been developed, it was then possible to begin the second phase of the research, which involved subjecting the hyperthreat to a modified threat analysis and response planning activity. In turn, this led to the development of PLAN E.
Strategic Logic
As a preliminary, the strategic logic for a threat framing approach needs to be expanded on. First, grand strategy—a notion subject to “endless debates”—generally refers to a type of statecraft that can “co-ordinate and direct all the resources of a nation.”14 It may comprise a plan, a set of principles, or a pattern of behavior.15 Grand strategy seeks to shape future events, rather than be shaped by them; it is proactive and creative in that it may involve creating the means to achieve desired ends.16 In this research, grand strategy was applied to both nation-states and to an assemblage of nations, such as those committed to the Paris Agreement of 2015.
Second, foundational Clausewitzian logic—that security strategy serves political objectives—is applied to the hyperthreat.17 To explain, what if the Paris Agreement and various climate emergency declarations are accepted as representing the will of the global populace? If these establish that global warming and ecological breakdown constitute a significant and urgent threat, then it follows that security strategy must reorient to support the larger political objective.
Accordingly, this research anticipates the civil sector requesting a new climate-environmental survival-based security strategy but cannot specify exactly how this would come about. Speculatively, a mandate could be achieved through multiple declarations of climate emergency by cities, regions, nation-states, or other groups around the world or through other, yet-to-emerge, new political concepts such as Extinction Rebellion’s proposed Citizens’ Assembly on Climate and Ecological Justice or political rewilding.18 Alternatively, militaries might initiate investigation as a part of contingency planning.
Prior Research: Climate-security Discourse Is Incoherent
The logic of extant approaches to geopolitical security has been seriously questioned since 1995, when the UN Commission on Global Governance suggested that “the concept of global security must be broadened . . . to include the security of people and the security of the planet.”19 Since then, expansive research on human and planetary security has ensued, accompanied by arrays of new projects, initiatives, and conceptual approaches, reviewed previously.20
Some further examples help outline the parameters of this discussion. Challenging the Copenhagen School ideas that “threats are socially constructed,” Maria Julia Trombetta argued security is also about “survival, urgency and emergency”—its meaning relates to context.21 Conversely, Joshua W. Busby cautioned on a loss of coherence when too many problems are placed in the “security box”; instead, he prefers a pragmatic focus—a careful analysis of the ways in which climate change might impact the state and the state’s interests.22 Alternate concepts include a human, gender, and environmental security approach (HUGE) or a focus on ecological security.23
More recently, ecological security research has morphed into the broader fields of existential threat, collapsology, and global catastrophic risk (GCR). GCR research examines potential “global systems death spirals”; linkages between global warming, food insecurity, and societal collapse; and has proposed that security must now be understood as relating to “the survival of humanity.”24 However, despite this wide-ranging planetary security literature and discourse, at the meta-strategic level, the speech act (of describing CEC as an existential threat) has yet to fundamentally alter humanity’s security posture.
Conceptualization remains a problem. A Swedish study concludes that climate security discourse is fragmented and incoherent for two main reasons. First, the discourse is constrained by a siloed structure where “different policy communities use different concepts to frame security risks posed by climate change,” while, second, there is limited institutional capacity to create cooperation and synergies.25 Examples of these different concepts, discussed by Malin Mobjörk et al., include resilience approaches; analyses of fragility, vulnerability, or insecurity; climate-resilient peacebuilding; and conflict-sensitive climate programming.
Analyzing the same problem, Lisa M. Dellmuth et al. find there is a lack of theoretical or empirical research on how to integrate the varied climate-security approaches that are found across different intergovernmental organizations (IGO) or to assess their effectiveness. They conclude that
there is little evidence that climate change has been coherently securitized across IGOs, and scholars’ debate whether we are witnessing a “failed securitization” of climate change or a “climatization” of specific security-related issues such as defense, migration, and development.26
Likewise, in overviewing practice, Joshua Busby identifies a patchwork of measures, including the United Nation’s “climate security mechanism,” which seeks to mainstream climate security considerations into general planning and integrated risk assessment procedures. Yet, he laments the lack of any systemic approach or solution: “the discussion of threats and policy initiatives begs the question of what to do.”27
Pertinent to climate-security discourse is other research on the gendered nature of both climate policy and traditional security.28 Collectively, this literature finds that climate policy and mainstream security approaches are predominantly conceived in hegemonic masculine terms, which emphasize the importance of science, economics, traditional hard power military approaches, and technical solutions. In contrast, coded as feminine are ethics and human and planetary security issues, which were rendered less important. Thus, gendered frames may distort threat perception.
A feature of prior discourse is persistent fear and suspicion toward securitization, which is often associated with top-down, simplistic, and draconian measures that would erode human rights.29 On existential risk, Nick Bostrom warns that
speculative risk mongering could be exploited to rationalize self-serving aggressive action, expansion of costly and potentially oppressive security bureaucracies, or restrictions of civil liberties that keep societies free and sane.30
Accordingly, military input has been limited to providing advice about the security impacts of a changing climate and environment and assisting with disaster response. In a report for the UN Security Council, an “informal expert group” of military advisors on climate security suggest their future role could involve providing “fine-grained, contextualized analysis” to UN agencies and helping to persuade decision makers on the need for action. They warn that if the UN Security Council fails to respond to the climate crisis, it will “appear out of touch with fundamental threats to international peace and security—and human survival.”31
Related to hesitation about securitization is research on climate action, which finds that doom and gloom narratives and top-down solutions may be counterproductive, while bottom-up transformative win-win narratives are better at motivating climate action.32
Climate-security literature often calls for a new approach. A wide-lens review of the United Kingdom’s security posture, which considered organized crime, infectious disease, financial stability, and climate change found that the strategy was “unbalanced” and its strategic moorings were “unsound.”33 In 2016, international relations practitioners issued an “urgent call for a profound restructuring of international politics and order that can assure the planet’s survival.”34 More recently, Simon Dalby argues that “traditional notions of security need a rapid overhaul,” and he advocates for a focus on decarbonization and making flourishing ecosystems.35 Such calls set new ambitions and seek a change of focus and priority, yet do not always describe what an alternate strategy might look like.
This research separates itself from prior work in five ways. First, the hyperthreat of climate and environmental change is centered as the primary threat, with the aim to find a pathway to a safe Earth (avoiding dangerous climate change and ecological collapse) in the context of other security threats.36 Second, the approach is scaled to the magnitude of the problem; it answers calls for a crisis or emergency response. Third, it applies a different and newly curated transdisciplinary lens to the problem, called entangled security, which acknowledges the interconnected nature of planetary, human, and state security. Fourth, economic actors are brought into the threat analysis process. Fifth, applying the deep framing research insights, creative, and description narrative techniques are used to convey the results via PLAN E.
Methodology
In broad terms, the hyperthreat was subjected to established threat analysis methods developed in military, security, and strategic studies, such as the military appreciation process (MAP) or the strengths, weaknesses, opportunities, and threats (SWOT) strategic planning method. However, these traditional methods were only used in a light manner; they provided the overarching analytical scaffolding within which more experimental philosophical and theoretical exploration could occur. Also, and akin to standard military planning practices, threat analysis methods were modified to first suit the unique circumstance being analyzed (the hyperthreat) and second to iteratively respond to the results of the analysis. An eagle-eye overview of the entire research project is offered below, which describes the steps taken but also highlights some of the key insights and subsequent decision points made about how to analyze the hyperthreat and develop strategic response ideas.
First, the research began with a critical inquiry into the risks of a threat framing. Exploration of linguistics; genocide studies; sociology; psychology; hate-crimes research; securitization theory; and militarization studies highlighted many risks, which peaked when threat was linked to a particular group identity. Yet, faulty threat analysis, whereby the nature of the threat was misunderstood, obscured, or manipulated also created risk, as it impaired capacity for effective response. Balancing these two sets of risks led to an approach that focused on harm-doing and actions that strengthened the hyperthreat, paired with a steadfast determination to avoid assigning threat identities.37
The second step was a preliminary problem scoping activity, which drew on the Joint Military Appreciation Process (JMAP) and design thinking to undertake an initial iterative frame-environment-threat analysis and center of gravity (COG) analysis.38 In analyzing humanity’s failures to respond effectively to climate and environment issues, and what might allow a seismic pivot, drawing on a range of climate policy and communication research, it was deduced that the COG for humanity to succeed was its “deep frames” (figure 1).39
Figure 1. Iterative frame-environment-threat analysis and COG determination
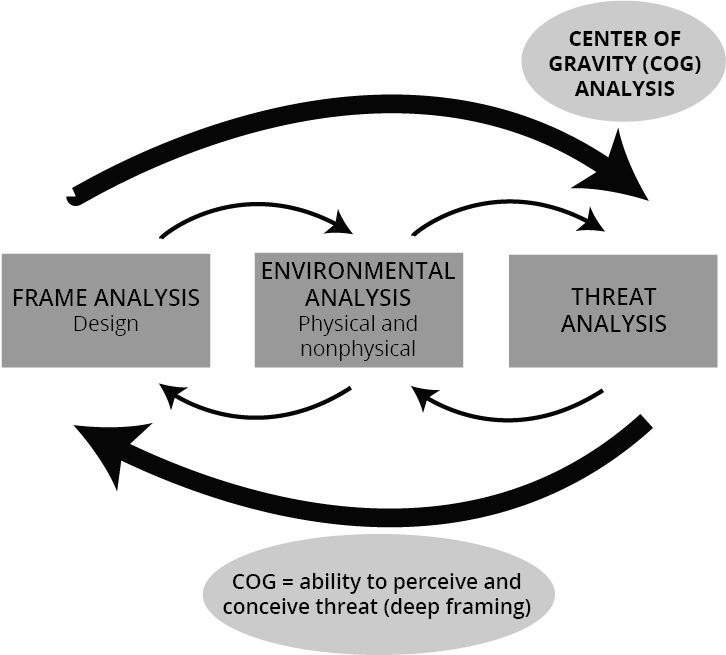
Source: courtesy of author, adapted by MCUP.
Accordingly, for the third step, research analytical activity narrowed its focus to one sole objective: the hunt for a new deep frame or way of conceiving threat and security in the Anthropocene. In simple language, to solve the COG problem, a new philosophy was required. Already discussed, and previously published, the first part of this was developing a new concept of threat—the hyperthreat frame. However, a wide body of other theoretical work (figure 2) helped to develop a new conceptual approach to security in an era of climate and environmental change, called entangled security.
Figure 2. Deep framing and threat—philosophical reset
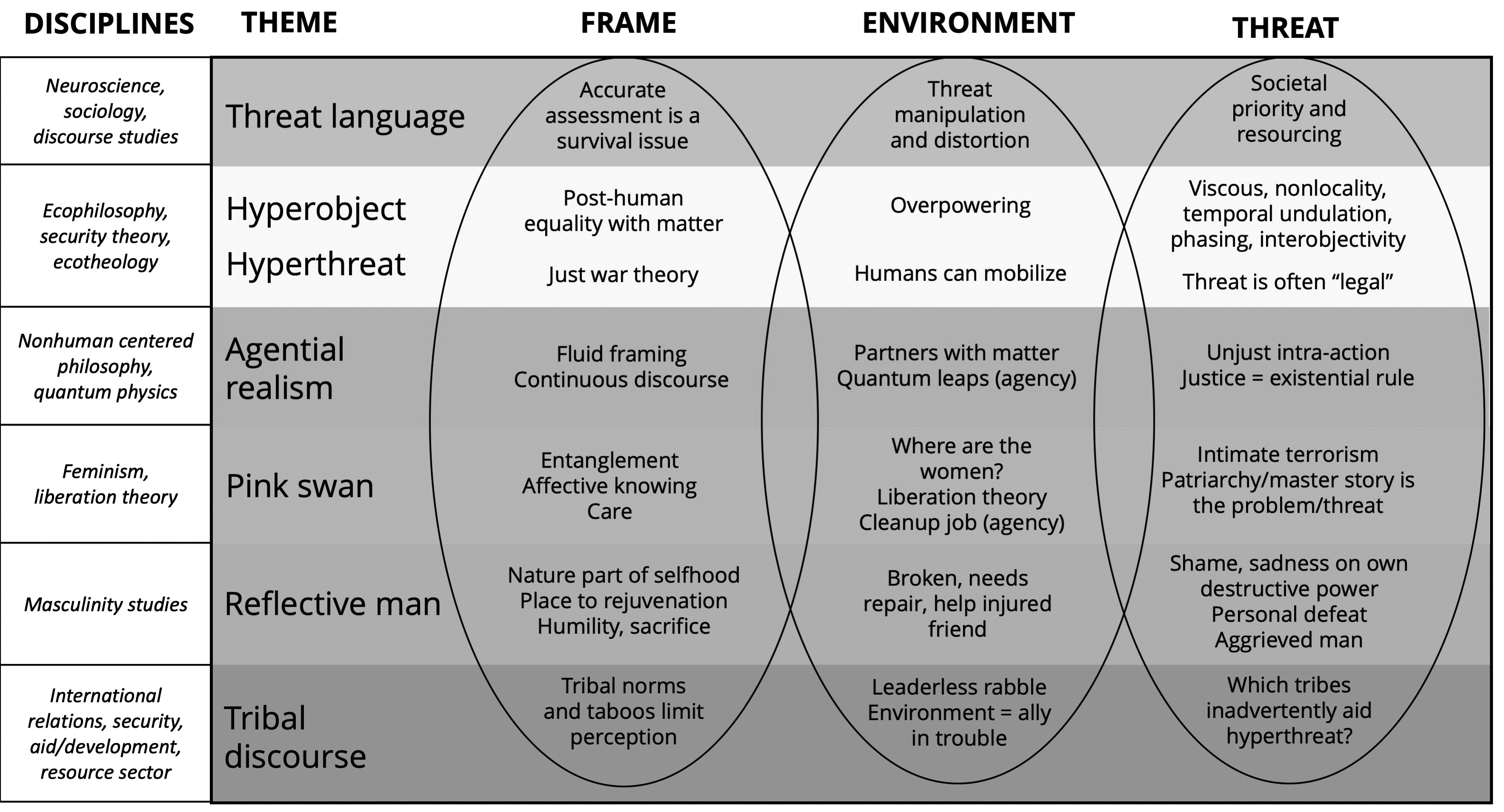
Source: courtesy of author, adapted by MCUP.
In its simplest form, entangled security appreciates that planetary, human, and state security are inherently entangled and interconnected (figure 3). Entangled security’s more complex theoretical aspects are summarized in figure 4.
Figure 3. Entangled security
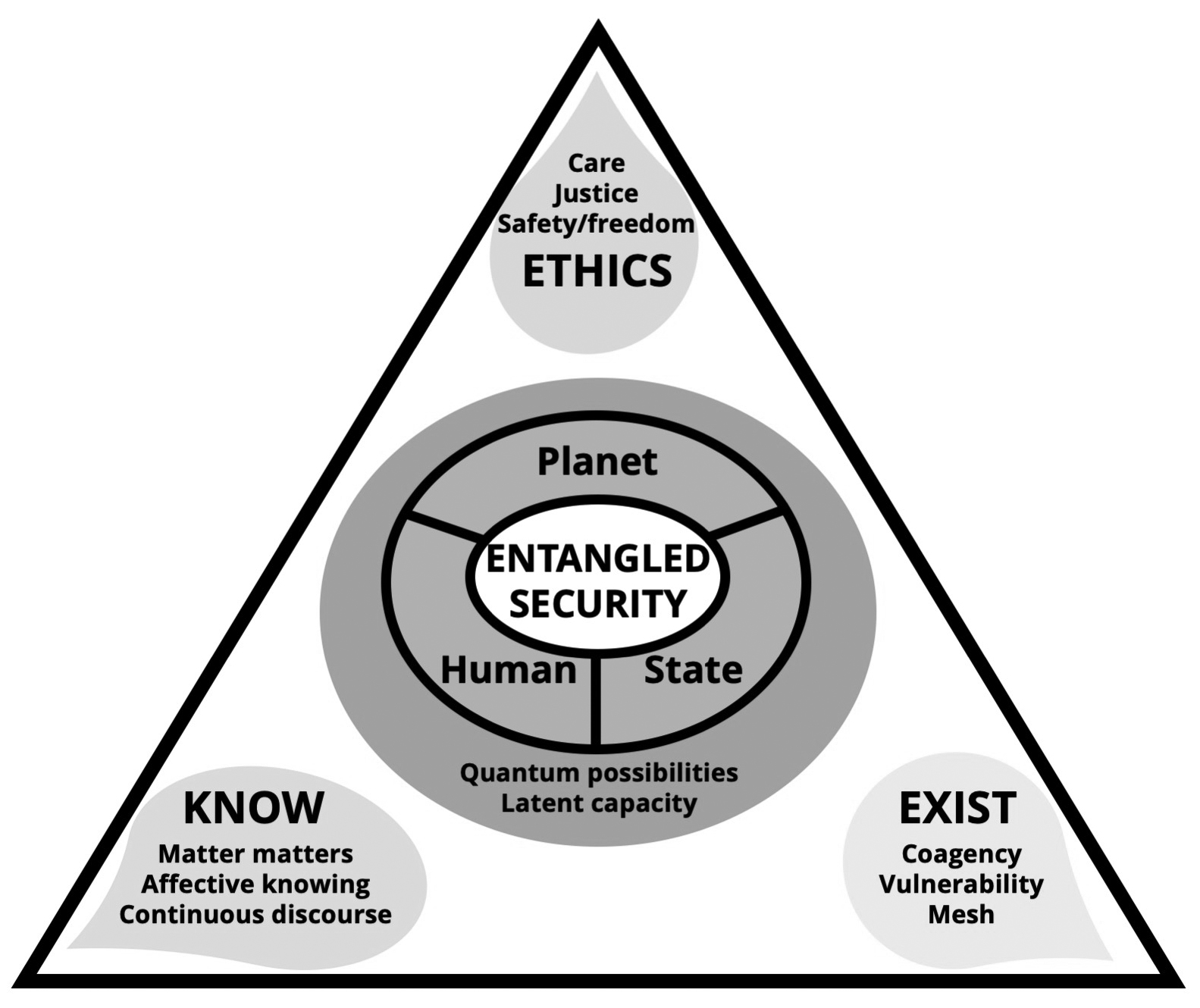
Source: courtesy of author, adapted by MCUP.
Figure 4. Entangled security conceptual compass
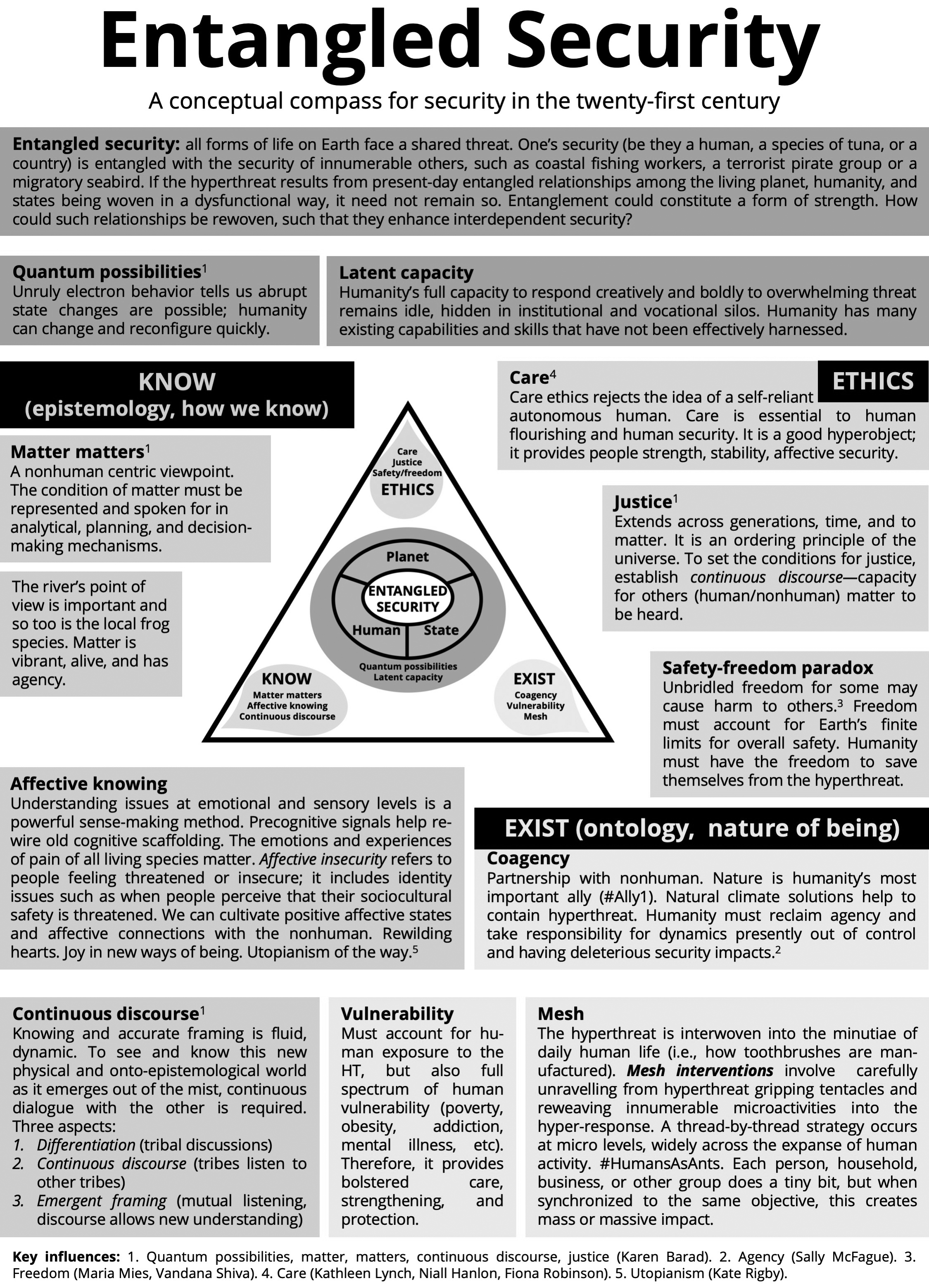
Source: courtesy of author, adapted by MCUP.
Once the new framing devices or theoretical approaches had been developed—the hyperthreat and entangled security notions—it was then possible to apply these concepts to real-world considerations.
Thus, the fourth step was effectively the environmental and threat analysis stage of MAP. The aim was to test and refine the developing theory but also to gain initial insight into the full nature of the threat and explore ideas about what a realistic, workable hyper-response might entail. In keeping with standard threat analysis protocols, two areas were explored: first, the threat context, and second, the general context. For the general context, a new analytical method was developed called a “tribal discourse.” The tribal discourse involved analyzing the hyperthreat in an entangled security environment, which meant considering the perspectives of people and organizations within each of the planetary, human, and state security sectors.
The fifth and final step saw the hyperthreat and entangled security frames placed into a strategic planning process (figure 5) to develop PLAN E. Analysis methods included a SWOT analysis; a principle of war analysis; a principle of entangled security analysis; and real-options analysis.40
Figure 5. Strategic planning and the hyperthreat
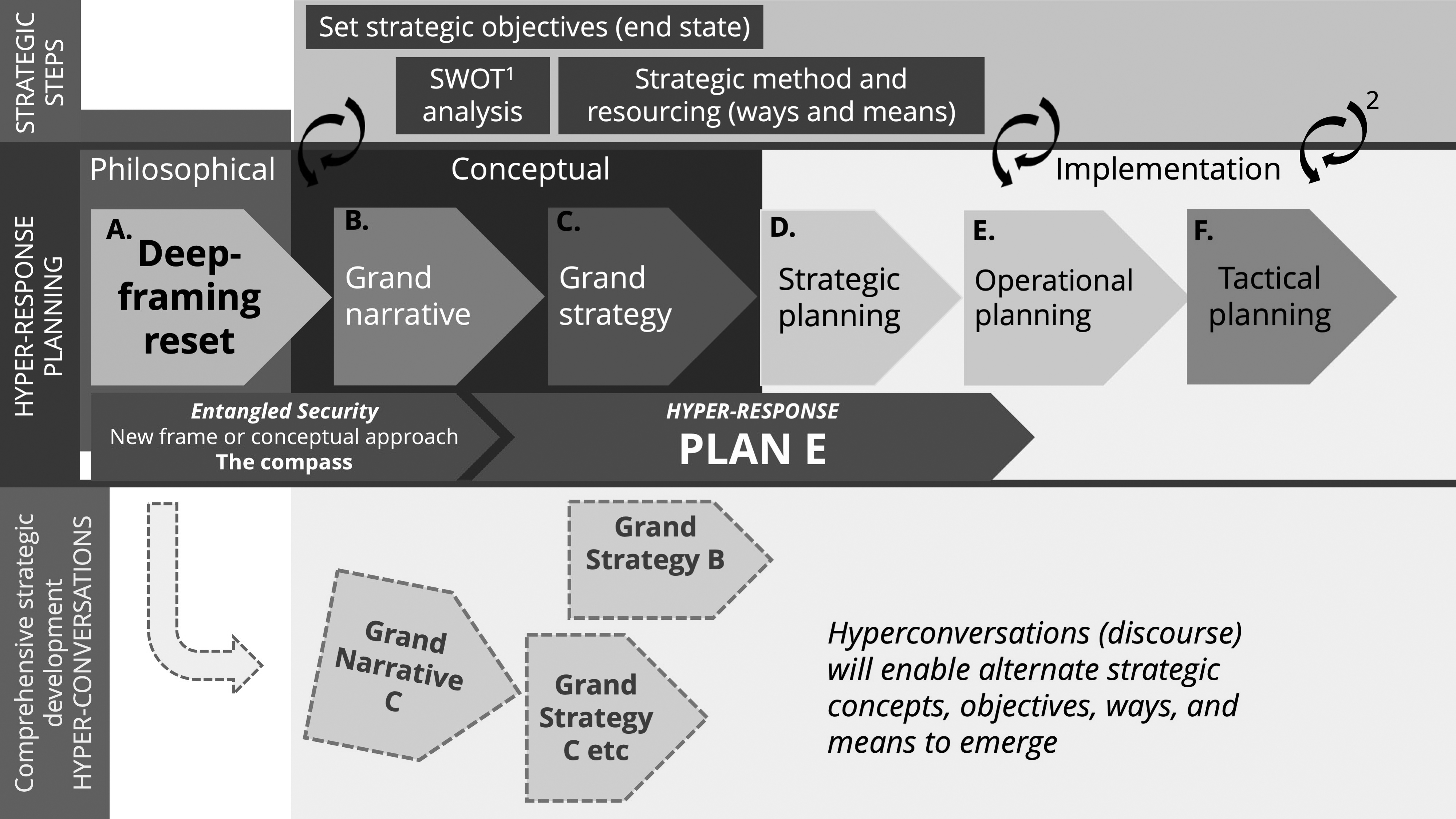
Source: courtesy of author, adapted by MCUP.
Research Outcomes
To recap, this research applied a modified MAP to the threat of climate and environmental change, which broadly comprised a frame analysis, an environmental analysis, and a threat analysis. The outcomes for the majority of the framing analysis activity (steps one, two, and three) have been briefly discussed above or published previously.41 Accordingly, here the article will report on the outcomes of the subsequent steps of the MAP and strategic planning process (steps three to five).
Step three—the final part of the framing analysis—was the development of the entangled security theory. Due to scope, it will only be possible to describe part of this theoretical development. The focus in this article is the most complex component—an introduction to “agential realism”; a new quantum science-based philosophy; and an explanation of how it informed the entangled security concept.
The analytical results from step four, the environmental and threat analysis process, will be described in more detail. Finally, step five, which involved strategic planning and creating a concept of operations (PLAN E), will be introduced.
Step 3: Frame Analysis—How Agential Realism Informs “Entangled security”
If deep frames and extant modern-era worldviews were preventing humanity from understanding its new threat context, there was a need to seek out innovators developing alternate philosophies that were more attuned to the nature of the Anthropocene. A key trend was removing humans as the locus of meaning and using insights that emerge from ecology and physics as the new philosophical bedrock and starting point. While Timothy Morton’s hyperobject notion conveys a nonanthropogenic-centered worldview and helps people to “think like a planet,” quantum physicist and philosopher Karen Barad guides us on how to “think like an atom.”42
Barad’s agential realism theory introduces the idea that, at the quantum level, the nature of existence is inherently dynamic, entangled, and subject to abrupt change. For example, it involves “unruly electrons” that may make quantum leaps. Matter—human or otherwise—cannot avoid impacting and colliding with other matter and thus inflicting “agential cuts”—that is, leaving a mark on the “other.” This is the “intra-active” and inescapably entangled nature of existence.43 If existence is like this, across her body of work Barad then explores the far-reaching implications it holds for ethics or notions like justice, time, and agency.
Highly pertinent to questions about framing and the hyperthreat, and building on Niels Bohr’s two-split experiment, agential realism also explores entanglement between matter and meaning.44 Barad proposes that meaning emerges through intra-active conversation between matter:
In an agential realist account, discursive practices are not human-based activities but specific material (re) configurations of the world through which boundaries, properties, and meanings are differentially enacted.45
Therefore, a quantum perspective instructs that because the nature of matter and existence has an effervescent, ever-changing quality, meaning making or conceptual development must also be fluid and responsive to the changing configuration of matter. Effective navigation of an entangled reality, Barad posits, requires “continuous discourse” between humans and all other matter.46
Agential realism has great significance for the question of climate and environment threat framing. It suggests that to be truthful, meaningful, and relevant, words such as “threat” or “security” must be part of the iterative reconfiguration of matter and meaning elicited by climate and environmental change. For example, if the intra-active impacts of greenhouse gases (GHG) (or forest clearing or plastic pollution in oceans) are harmful to other forms of life, then this must be captured within a discourse that is alive to the realities of material reconfiguring of life on Earth. In other words, it simply cannot be that while matter is undergoing seismic changes and having substantial agency and intra-active impacts, that old notions of threat or security remain stagnantly fixed to material conditions of a preclimate era.
Agential realism requires a nonhuman-centric approach to security and threats. However, it also expanded conceptual territory and allowed new questions to arise. For example, if harming other matter is more easily conceived as also hurting oneself because everything is entangled, what does that mean for how to consider a threat? In an entangled ethico-onto-epistemology, is the most significant form of threat one that, like a cancerous cell, has the potential to endanger the wider web of intra-active matter?47 What does an agential realist perspective mean for the notion of an “enemy”? Is enemy activity best conceived as actions that harm another entity’s freedom of movement across an entangled web or its ability to intra-act—to exchange resources, to participate in intra-active becoming? Alternatively, by accepting entanglement, does this at least dilute and, at most, erase the whole notion of enemy? Could the concept of enemy be replaced with a range of new ideas and words that match entangled existence?
Overall, agential realism provided a rich conceptual space to review the idea of threat and reimagine threat response. It contributed six principles to the entangled security theoretical approach: the idea that “matter matters”; entanglement; the elevation of the principle of justice; the idea of quantum possibilities (random state changes); the need for continuous discourse for ongoing, accurate framing; and the idea of coagency—new forms of partnership between human and nonhuman matter.48
Step 4: Insights from Environmental and Threat Analysis
The Hyperthreat and the Threat Context
The hyperthreat sits within a threat context featuring increasing insecurity and instability. Global governance systems are less stable. The legitimacy of the global liberal, rules-based order, which was perceived as skewed in favor of Western nations, is fading.49 Levels of democracy and freedom have deteriorated.50 International organizations (IO) are finding themselves not fit for purpose, while those that oversee climate and energy issues face doubts about their legitimacy.51
Human insecurity is widespread. The poor as well as some women, ethnic, and cultural groups and other vulnerable groups face multivarious threats, which include domestic abuse, sexual violence, human trafficking, slavery, pedophilia, and hate crimes.52 Efforts to address these problems have been stilted and slow.53 Other concerns include the stability and fairness of global fiscal systems; artificial intelligence (AI) unaligned with human values yet surpassing human controls; and emblemized by the COVID-19 pandemic, increased risks and exposure to infectious disease that are linked to the ascension of the hyperthreat.54 Analysis of 2018 UN Sustainable Development Goals (SDG) progress has found that, in the precoronavirus pandemic period, SDG achievement was undermined by two key factors: the early impacts of global warming and a deteriorating security environment.55 Critically, as security degraded, helpers (from all ranges of nongovernmental organizations [NGOs] and development agencies) were hindered from undertaking their work, while climate and environmental impacts added another blow.
The 2021 SDG report found that the pandemic led to even more backsliding, especially in relation to poverty, food insecurity, and health. While there was a temporary dip in GHG emissions, and while there were more financial resources allocated to climate action, the GHG growth trend resumed, with the pace of change still “woefully offtrack” to achieve the Paris Agreement objective to limit warming to 1.5 degrees Celsius. Overall, the climate and ecological crises continue unabated. In short, human vulnerability is increasing, while current methods of addressing interconnected SDG are proving inadequate.56
Affective insecurity is increasing, that is, global citizens feel less safe, physically and philosophically. Significant philosophical revisions and understandings of social and individual identity and freedom are under way, which unsettles peoples’ sense of epistemological, ontological, and affective security. Psychological warfare and information operations, waged by multiple actors, including corporations, erode trust in institutions and perceptions of reality.57 Other facets of this problem include conspiracy theories surrounding a corrupted global elite; a rise in domestic extremism; and the general psychological strategy of terror groups to disturb citizens’ experience of feeling safe.58
Humanity is distracted from the hyperthreat by an increasing number of intrahuman tensions and violent conflicts. According to the Stockholm International Peace Research Institute (SIPRI), in 2020, after a decade of growth, world military spending totaled $2 trillion.59 This spending reflects a general deterioration of the global security environment, but also expectations of greater conflict during the 2022–30 decade. Influential factors include a persistent baseline of many fragile states; increasingly sophisticated violent nonstate actors and the heightened prospect of major intrastate warfare, such as escalation of the Ukraine and Russia conflict; or war between the United States and Russia or China, or as some speculate, an Iran-China-Russia alliance against the West.60 Such tensions could simmer along as “hot peace” style tensions, involving cyber interference and economic coercion, which could escalate to nuclear war. Alternatively, as John Keane postulated, in the case of China, relations may transition peacefully into a new world order featuring a powerful yet nonviolent Chinese “Galaxy Empire,” which features some despotism mixed with Confucian inspired benevolent ideals.61
Regardless of what transpires, extensive preparedness for warfare during 2022–30, including expensive space war initiatives, will still drain much of humanity’s intellectual, technological, and economic resources while also likely imposing continued pressures on Earth’s climate and ecology. This occurs at the exact same time that transformative response to the hyperthreat is required. Thus, serious preparations for warfare, or actual warfare, risk impairing or crippling capacity for effective CEC hyper-response. Accordingly, a significant insight is that the current global military buildup could represent a situation whereby many nations are entering, unconsciously or perhaps because there seems no other option, into a new type of mutually assured destruction scenario.
A final feature of the threat environment is dubious capacity to restore peace—to fix societies once broken. The Intergovernmental Panel on Climate Change (IPCC) previously claimed that there are “well-established strategies for managing violent conflict that are effective but require significant resources, investment and political will.”62 However, security analysts would caution that it is not that easy; it has not been possible to restore security in places like Syria, Afghanistan, Iraq, Honduras, or the Democratic Republic of the Congo, despite considerable resources having been spent and exhaustive political and diplomatic efforts attempted. This example reflects not only siloed and faulty threat analysis processes, but it also highlights the possibility that humanity has lost control of their capacity to achieve security and safety—echoing Morton’s fundamental conclusions—that humans have lost agency to the hyperobject.
Tribal Discourse and General Context
Aside from the threat context, to understand the general context more deeply, and to apply an entangled security lens to this process, a new analytical method was developed called a “tribal discourse.” Tribal discourse allowed analysis of key generic human tribes involved in an entangled security context, to explore their stance in relation to the hyperthreat (figure 6).63 Overall, it was found that although many tribes are engaged in minor operations against the hyperthreat, unfortunately, humanity’s most powerful tribes (those with a state security orientation) often abet the hyperthreat. Select analytical insights follow.
Figure 6. Tribal discourse
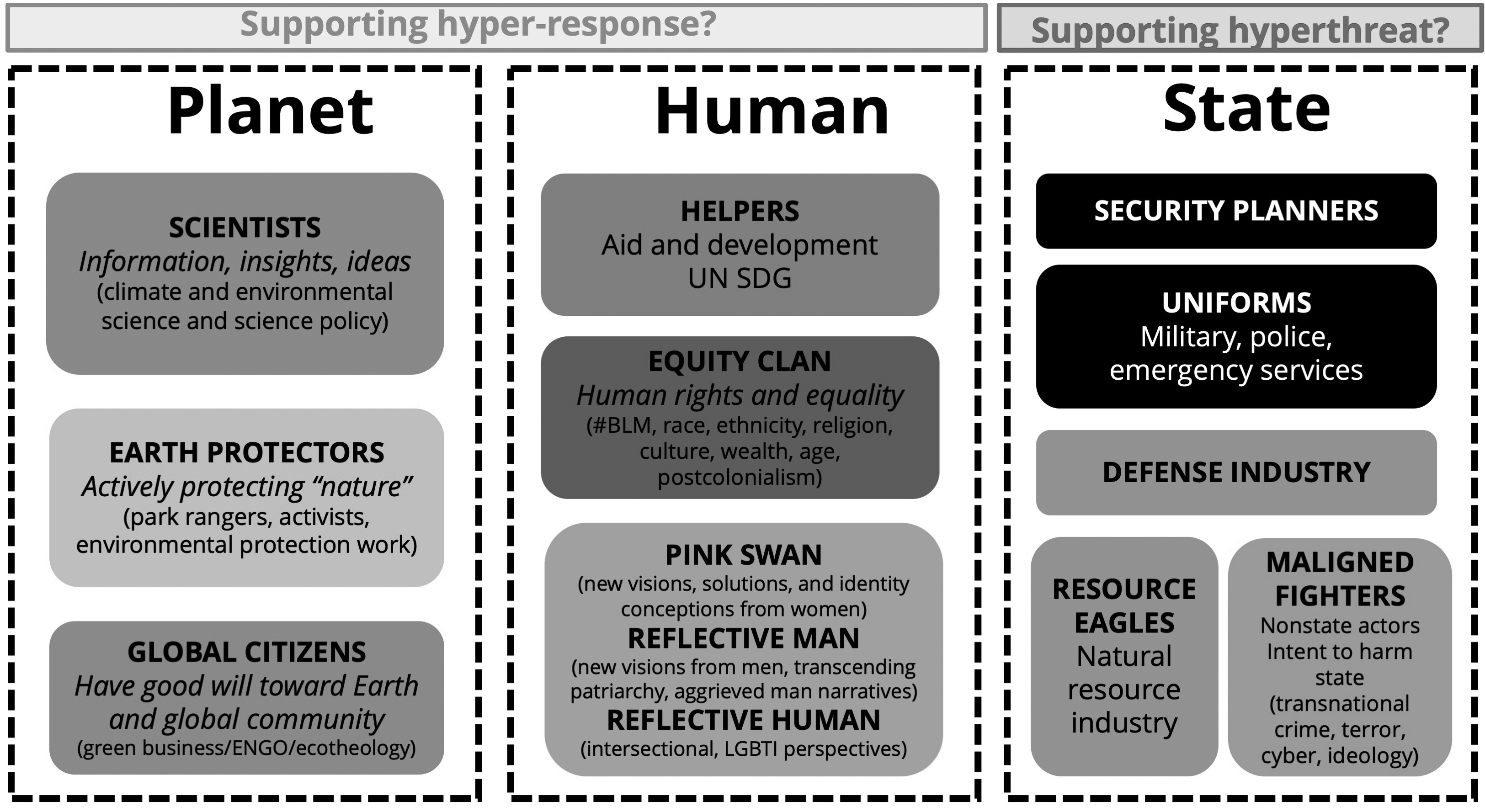
Generic tribes loosely grouped by their primary security foci and stance in relation to hyperthreat.
Source: courtesy of author, adapted by MCUP.
Planetary Security Tribes
Considering planetary security, scientists struggled with bridging the science-to-policy gap, and while global citizens showed great potential, at a global level, they still lacked the impact needed to contain the hyperthreat.
Of grave concern, however, and pertinent to a threat inquiry, was the circumstance of the “Earth protectors” who face an increasingly sophisticated, well-resourced, and sometimes militarized human threat.64 Between 1996 and 2016, there were persistent annual growth rates in global environmental crime.65 With an estimated market value of between roughly $90 to $276 billion U.S. dollars per annum, environmental crime is perpetuated by corporations, corrupted officials, and transnational criminal and terrorist networks.66
An increasingly quasimilitary style of operations has, in turn, led to green militarization.67 Environmental crimes have cascading negative impacts: illegal logging and deforestation reduce carbon sinks, while crime networks undermine nation-states’ governance capacity and legitimate income. Although occasional progress is made, overall, the literature portrays a sense that frontline agencies are overwhelmed.68 For example, proponents of Botswana’s controversial shoot to kill policy to address rhinoceros poaching argue that such approaches must be understood in the context of all other measures failing.69
As CEC impacts worsen, wilderness becomes rarer but also more lucrative. Correlated with degrading human security, environmental crime becomes a perverse new form of employment. Conceptually, new battalions of environment criminals are being raised, with greater technological and military capability, who are effectively aligned with the hyperthreat; that is, they increase its destructive power.
Human Security Tribes
As global instability and insecurity increases, the capacity of human helpers (the aid and development sector and the human protection regime) is also in decline.70 When combined with the prospect of harsher hyperthreat impacts to come, this creates a downward spiral, called the Helper Hyperthreat Bind (figure 7), which must be considered a red flag.
Figure 7. The Helper Hyperthreat Bind
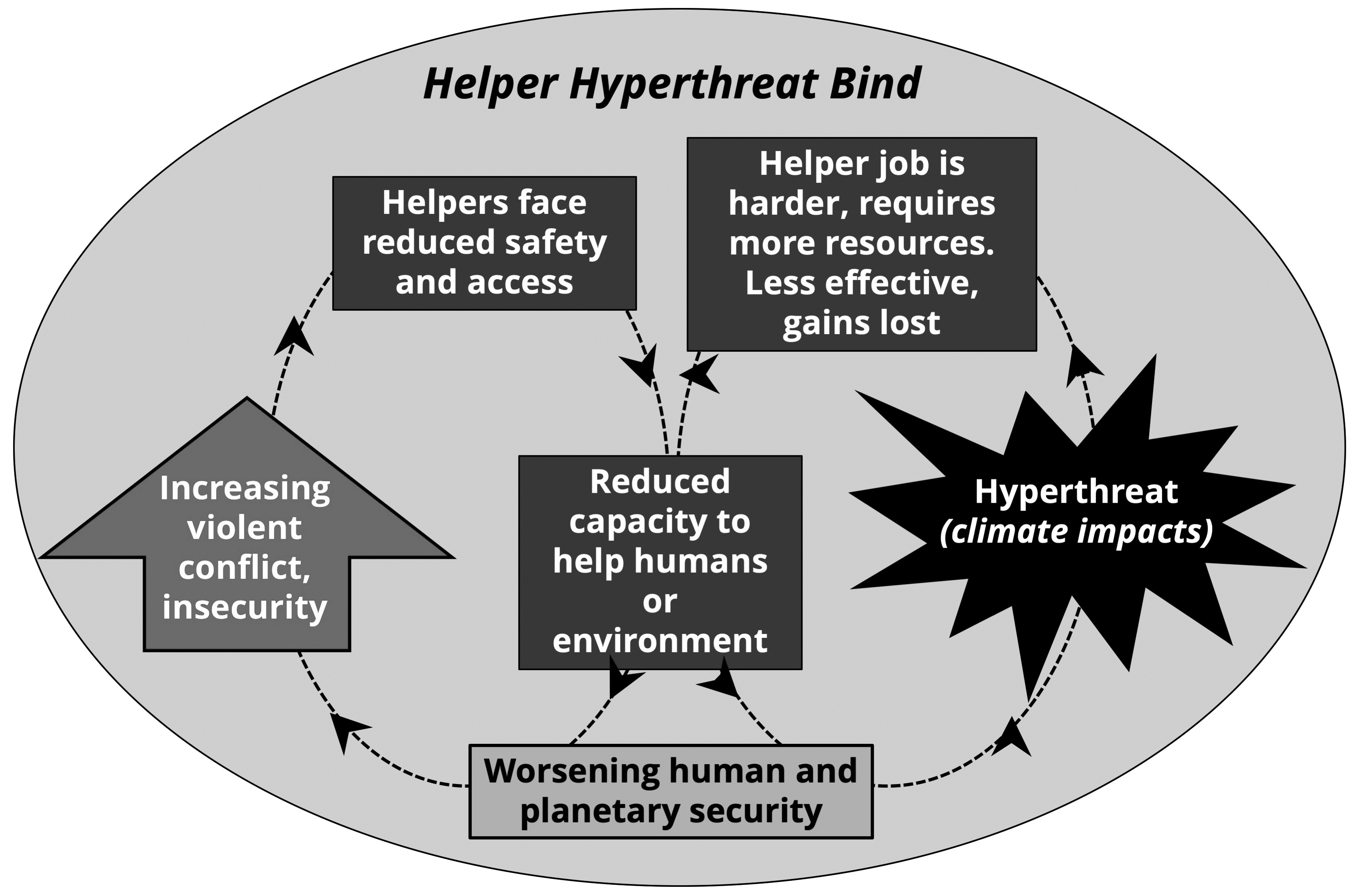
Source: courtesy of author, adapted by MCUP.
Analyzing potential consequences, one question is how a lack of help may be perceived by the most vulnerable. At best, nonhelping might be accepted as a noninterventionalist strategy. However, there is also the risk that nonhelping is perceived as, or manifests as, a strategy that appears to leave people to suffer, or worse, graduates to, by default or nonaction, to a let them die strategy. If it became evident that this was occurring, this in turn would likely legitimize a sense of grievance toward the developed world, which could manifest in destructive ways or be exploited by malevolent agents. The strategies of nonintervention or nonaction could also create a permissive environment for the worst forms of human behavior to emerge, such as genocide, slavery, and other forms of abuse. There are already early indicators of a link between global warming, or the onset of the hyperthreat, and increasing levels of slavery.71
However, another possibility is that the current structural quagmire of international organizations, humanitarianism, and the delivering of help could be interpreted as an opportunity to reorganize the systems of help, long criticized as constituting new forms of colonialism.72
State Security Tribes
Maligned Fighters
For state security tribes, of concern is a prospective quasi partnership between the maligned fighters (nonstate actors with intent to harm others) and the hyperthreat; two examples help explain. The first is an analysis of nonstate armed groups in the Lake Chad region, Syria, Afghanistan, and Guatemala that concludes that global warming (the hyperthreat) is contributing to creating an environment in which such groups (maligned fighters) can thrive.73 The second is the trend of terror groups’ (maligned fighters) integrating control of environmental resources into their tactics, such as water or, less successfully, oil, which could be viewed as an early warning of a type of tactic that might be developed further during the next few decades.74 Outside conflict zones, malevolent control, or disruption of environmental resources, can occur through targeting critical infrastructure.
State Security Tribes Misaligned
The most significant finding from the tribal discourse analysis was the incongruent stance of state security tribes, a claim that requires greater articulation through an introduction to three concepts: material security, systems maintenance, and dual-logic.
Material Security
Material security refers to the goods and natural resources (e.g., food, timber, steel, fuel, fiber, minerals, paper, etc.) that assist human societies and the nation-state to function at a practical level. A crucial part of twentieth-century material security thinking, borne of experience, and which became hardwired into security planners’ minds after World War I (WWI) and especially World War II (WWII), was the idea that oil is essential for military victory.75 Potentially, current security and strategic approaches remain moored to this guiding worldview or deep frame, which links fossil fuels with security—an idea which is now at odds with countering the hyperthreat. More generally, after WWII, for Western nations at least, the state tribe’s role in ensuring material security for their citizens was understood as an ethical undertaking—part of the postwar rebuild and resources for freedom narratives.76 In the 1970s, due to a combination of oil shocks and limits to growth discourse, material security started to have greater ramifications for international relations and security policy.77
Systems Maintenance
A generic term to describe the security sector’s role in material security is Doug Stokes’s systems maintenance construct.78 Stokes explains that as global supply chains became more vulnerable to disruptions, there was an increased global commons argument to use tools of force, like the Central Intelligence Agency (CIA) and the U.S. military to maintain the system. This phenomenon has also been described as a modern-era Lebensraum strategy, while others argue the logic also infuses stabilization operations.79 Thus, under systems maintenance logic, protecting the hyperthreat has historically been regarded as a necessary and dutiful service to the nation.
While system’s maintenance may be enacted in a way that is not deleterious to others, this is not always the case. Stokes finds systems maintenance approaches have led to human rights abuses and more authoritarian regimes.80 The problem also needs to be considered alongside resource war literature and related testimony from a so-called economic hit man.81
The link between the 2003 Iraq War and oil, officially denied but best understood through Jeff D. Colgan’s nuanced analysis, especially his causal pathways framework, is highly significant to hyperthreat deliberations.82 Through a systems maintenance prism, the 2003 Iraq War can be viewed as being a war waged in support of the hyperthreat. Ironically, and revealing an incoherent grand strategy, at the same time this expensive quasi resource war was waged, global citizens (people with good will toward Earth and its global community) were developing new ways to achieve material security (ecoinnovations, zero-emission technologies), which would have benefited from greater resourcing and support from state tribes to be fully realized. Therefore, in simple terms, instead of going to war to secure fossil fuel resources, hypothetically and in hindsight, energy security could have been achieved through investing the same amount of government resources into a massive transition to renewable energy technologies and ecosensitive design, which would have also helped contain the hyperthreat.
Most concerning to PLAN E is that despite new awareness of the hyperthreat and the increasingly counterproductive effects of system’s maintenance, the state tribe trajectory remains largely unchanged. The nonprofit group Global Witness finds that resource eagles (the natural resource sector) are set to invest $4.9 trillion USD on exploration and extraction of new fossil fuel resources from 2020 to 2030; yet, the report argues that none of this additional activity can occur if global warming is to be limited to 1.5 degrees Celsius.83
The current buildup in global military spending, reflects uniforms (militaries, police, and emergency services worldwide) preparing for multiple conflict scenarios, many of which have systems maintenance dimensions. For example, the South China Sea dispute relates to control of shipping lanes and rich fisheries, but also access to the sea’s natural gas and crude oil resources.84 Furthermore, “Almost a third of global crude and over half of global liquid natural gas (LNG)” passes through the South China Sea, which includes 80 percent of China’s crude oil imports and may contain “more oil than any area of the globe except Saudi Arabia.”85 Likewise, Russia’s interests in the Arctic and China’s interests in Antarctica and Africa revolve around material security concerns. In simple terms, extant military strategy supports a race for remaining resources, which could destroy what is left and imperil all.
Dual-logic
The above discussed incongruency leads to the expansion of Doug Stokes’s concept of dual-logic.86 Business-as-usual approaches to material security, which impose a system’s maintenance burden on security agencies, poses two threats to humanity: one, intensification of hyperthreat power, and two, increased likelihood of geopolitical security destabilization and conflict.
In contrast with prior climate-security literature that considers whether CEC may lead to violent conflict, dual-logic suggests that, instead, the failure to rapidly transition to ecologically sustainable pathways, when first prominently identified to the global community as a type of security issue in the late 1980s to early 1990s, may already have had security impacts.87 While impossible to prove, such an insight must inform state tribes’ positioning in relation to the hyperthreat henceforth.
Overall, centering the hyperthreat as the most significant threat reveals that state and security tribes, humanities most powerful groups, are inherently misaligned with their raison d’être—protecting their human and nonhuman populations. To explain clearly: though many state tribes facilitating fossil fuel intensive infrastructure and harmful natural resource extraction to meet the material security needs of their populations, they inadvertently empower the hyperthreat.
Research on climate denialism highlights how state tribes can be hypnotized by the hyperthreat.88 Through systems maintenance security operations, the uniforms facilitate hyperthreat growth. In undertaking disaster response roles, increasingly, uniforms also find themselves cleaning up after the hyperthreat. Security agencies do not reorient toward this new foe; rather, they remain its ally and its protector. Yet, if this strange, incoherent situation could be reversed, if humanity could reclaim and reorient its state tribes, the current balance of probabilities, which currently lie with a hyperthreat victory and a hothouse Earth outcome, could be recast.89
Threat Analysis: New Ways to Think about Threat
The research found that the underpinning ways in which a threat is commonly understood, at the deep framing level (subconsciously held entrenched worldviews) is now mismatched to the way in which threat (violence, destruction, harm) will increasingly manifest in the twenty-first century. New ways of understanding threat are required, which in turn can inform what a new threat posture might look like; reflections on this are offered below.
Harm-doing defies conventional expectations of what a threat or what harm looks like. Akin to Hannah Arendt’s description of the “banality of evil,” with the CEC hyperthreat, there is the problem that those making the most shockingly harmful decisions do not look like an enemy or threat.90 Rather, they may be a jovial person who volunteers at the local school clean-up day and bravely overcomes a cancer scare. There is also the problem that such decision makers exist on a spectrum from those who unconsciously participate in harmful decision making to those who do so knowingly yet sit within the law and those who are consciously undertaking harmful and illegal activity yet enjoy virtual impunity due to a lack of institutional capacity to address such harm.
Recalling the Stanley Milgram experiment and the way in which people readily defer their ethical decision making to respected authority figures, another factor could be that key decision makers who are consciously or inadvertently aiding the CEC hyperthreat may hold sanctioned authority, trust, and power.91 Such decision makers may be a CEO or government official who wears a smart suit, exudes a sense of gravitas, and whose narratives orient around making valuable contributions to society. Yet, despite rhetoric and appearances, the decision making could be devastatingly destructive and threatening to many people and forms of life. This could be the greatest challenge to defeating the CEC hyperthreat: the awkwardness of confronting wrongdoing when it appears proper, with all the symbols of societal authority and validation. There is an incapacity to see threat when it is not dressed like a threat.
For modern Western nations, a particular challenge may be that, in official policy statements at least, it persistently perceives itself as the “good” protagonist, dedicated to upholding a liberal, rules-based order. The threat is predominantly characterized as some form of other, which exists not within but elsewhere. Accordingly, in the era of CEC, a most confounding idea is that this time the threat not only looks like oneself but is also within one’s own society. This threat analysis presents a very difficult narrative conundrum, which, it is argued here, itself constitutes a highly significant aspect of the problem. Accordingly, there is a need to find a way to discuss and resolve these issues in a way that does not dehumanize people, nor create ruptures to the sense of trust and cohesiveness within society.
As alluded to earlier, a key conclusion from this research was that because of the dangers of threat narratives, because the Paris Agreement depends on a spirit of cooperation, and because accurate threat analysis is important to humanity’s survival, it is argued that the CEC threat focus should shift toward neutral identification of harm-doing. The key difference is that for CEC, a threat is not conceived as an identity (an individual or group). Rather, threat analysis and response planning can focus on actions that will harm others (including matter) or that will degrade planetary-human-state security.
Identification of harm-doing is merely step one. When it comes to preventing harm, a series of graduated responses would need to be developed. Because of the unique way in which the CEC hyperthreat manifests, at the lowest scale, ideally, this is bookended by a harm-to-help ethic. To explain, this would involve assisting entities to transition their activities from inadvertent CEC hyperthreat support toward being part of the CEC hyper-response. This acknowledges the way in which the CEC hyperthreat is interwoven with extant economic, governance, and security systems and the multifarious ways in which people participate in harm-doing. At the other end of the scale, an issue that will become increasingly important is the need to consider stronger mechanisms to address deliberate sabotage and the undermining of effective CEC hyper-response.
Turning to the nation-state, if new ways of considering threat are required, which match the unique nature of the CEC hyperthreat, then a novel approach would be to consider the nature of the power relationship between the state and the CEC hyperthreat. A relevant conceptual model comes from research on domestic abuse. The Duluth Model is a widely used tool to explain the components of abusive relationships, where power and control over another person is exerted in multiple ways.92 It can be applied to CEC to inform deliberation on how to strengthen the state’s capacity to counter the hyperthreat (figure 8).
Figure 8. Hyperthreat—behaviors and impacts of the worst enablers
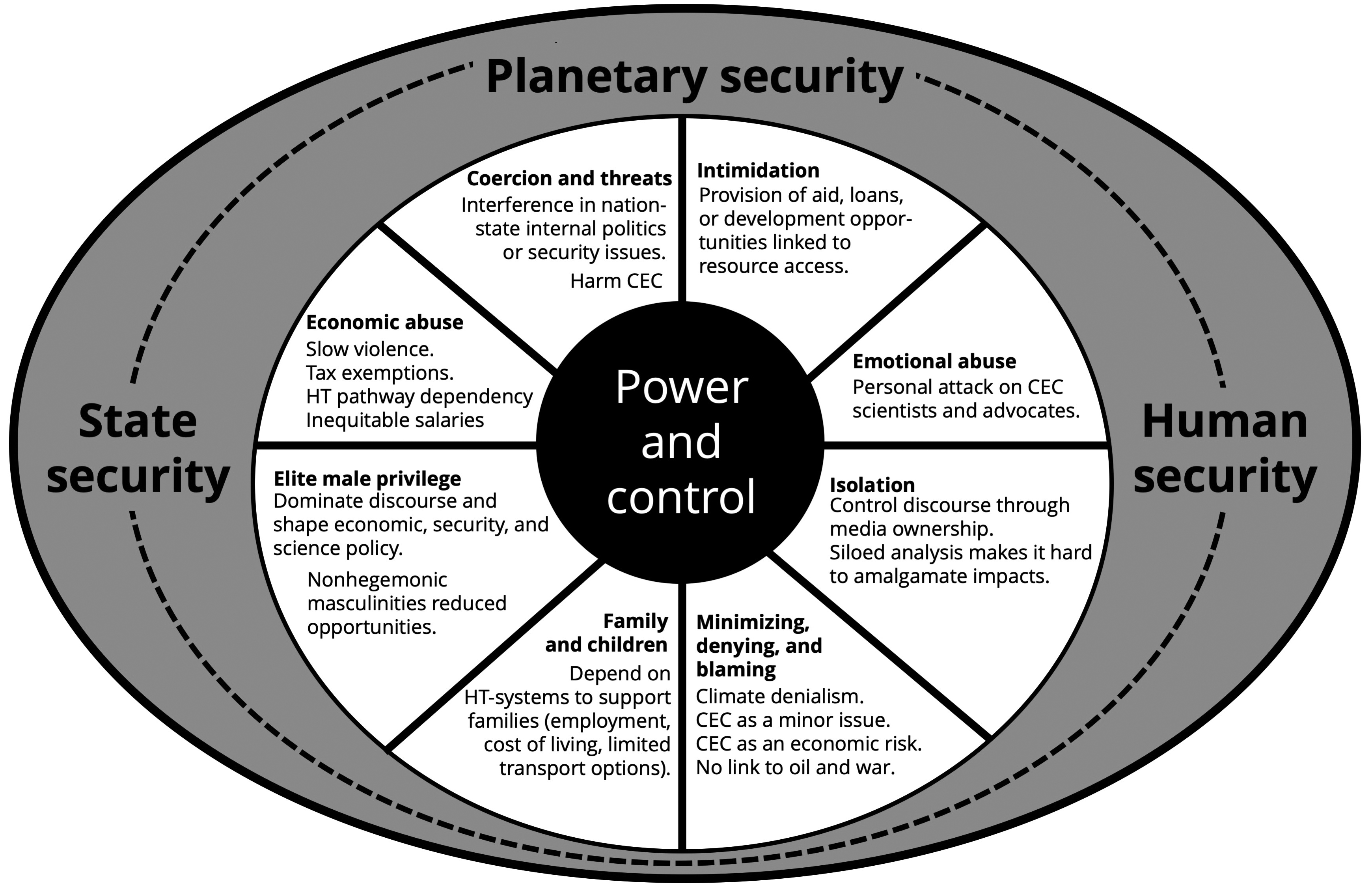
Source: courtesy of author, adapted by MCUP.
Step 5: Strategic Planning—Development of PLAN E
To demonstrate the potential of a new conceptual approach that centers climate and environmental change as the main threat and uses the new hyperthreat and entangled security framing devices, strategic planning methods were used to develop a prototype new grand strategy to counter the hyperthreat, called PLAN E.93
PLAN E must be understood as a test of a new conceptual approach rather than a definitive plan. The conceptual work—the initial scoping, frame, and threat analysis of this research—is envisioned as contributing to what military planners consider the starting point for developing a strategic response to a threat. Developing a comprehensive strategy would require a larger activity, involving wide disciplinary expertise and support by arrays of intelligence, scientific, and other research institutions and whole of society capabilities. Nonetheless, this initial pilot activity reached some new insights and approaches as discussed below.
In contrast to the previously discussed literature that warns of the risks of securitization, such as top-down, rigid approaches that impinge on human liberty or creativity, PLAN E presents a security strategy that could be described as predominantly a bottom-up solution. The research identified risks with globalized, overly centralized control, such as little redundancy in the case of tyrannical elements gaining control of global levers of power and pragmatic implementation difficulties. The proposed grand strategy incorporates restoring nation-state agency and focuses upon ecomultilateralism, or regional solutions.
PLAN E is civilian led and involves civilian mobilization, which is distinct from militarization. Military forces would be partially reconfigured as part of this strategic realignment and will form a portion of larger hyper-response forces (HRF).
PLAN E is concerned with meta-level grand strategy, and at this level, proposes the guiding general idea that security conception, response planning, and actual response increasingly needs to return to the broader population and to local levels. Decision making and resources would increasingly be devolved. This is due to the localized ways in which the hyperthreat manifests and the prospect that future security forces may be less deployable due to extreme weather impacts on transportation infrastructure; the impacts of future zoonotic diseases and pandemics on travel; and the need to reduce GHG emissions associated with large deployments of personnel and equipment.
Further, localized security forces and capabilities takes into account the need for timely responses to hyperthreat-related disasters; the importance of local knowledge in effective response; the types of skill sets needed, which often are within the civil sector; and the general trend toward localized, distributed solutions and circular economies as part of zero emissions and ecologically viable pathways for the broader population. Redundancy is achieved through dispersion, with local and regional capabilities having capacity to deploy, at least, to neighboring regions, towns, or cities impacted by hyperthreat assaults. This bottom-up focus does not negate the need for nationalized capabilities and some globalized components within a strategic response; the design can be regarded as a shift of security resources toward the places where the hyperthreat strikes.
Overall, the research began with seeking to understand the new security environment and problem and then consider the capabilities needed, in broad form. Exactly which roles are civil, military, or dual is the type of granularity that requires separate detailed analysis. However, some initial thoughts on how militaries might adjust to a hyperthreat context can be offered now.
Future security forces may increasingly locate in their home communities. This might address the problem of poorer communities being disproportionately represented in militaries and other burdens associated with continued personnel postings and relocation. Additionally, PLAN E also anticipates that as hyperthreat impacts become more severe, many military personnel will want to be near their families and communities.
Other significant features of PLAN E are the raising of new capabilities, especially in planetary security and in combating financial and legal dimensions of the problem. While military forces are already used to protect the nonhuman (e.g., patrolling fisheries), PLAN E incorporates far more extensive and robust protection of the nonhuman (soils, rivers, forests, grasslands, marine species, agricultural areas, zoo animals, pets and all sorts of flora, fauna, and other “matter”). The difference is that protection is not merely oriented toward protecting resources for human consumption, but rather recognizes that nonhuman forms of life are sentient beings, deserving protection in their own right, and who deserve to live without unnecessary cruelty or suffering on their home, Earth.
To provide a tangible example of how planetary security might relate to a U.S. Marine context, consider the forthcoming 2022 UN Ocean Conference, which will consider the proposal that at least 30 percent of the global ocean is designated as marine protected areas (MPA).94 What type of security threats will MPAs face, and what type of capabilities will be required to protect these areas? How might illegal offshore oil and gas mining or illegal deep-sea mining occur in the decades ahead? Could such activities be protected by armed militia? If so, how might civil agencies stop and dismantle such operations and what type of security support might they require? Similar questions arise for all of Earth’s ecosystems, with the IPCC’s 2022 report stating that their “resilience . . . depends upon . . . conservation of 30% to 50% of earth’s land, freshwater and ocean areas.”95 PLAN E and the proposed HRF aims to provide a conceptual approach and structure that creates space to routinely conduct threat analysis and response planning, which is attuned to these new geopolitical policy imperatives and an entangled security context.
Discussion: Accurate Threat Perception Remains Elusive
The research concluded that the capacity to see and understand threat, at the start of the twenty-first century, is distorted at many levels and that this hinders the capacity to understand the full threat spectrum and design optimum strategy.
Reframing CEC as a hyperthreat and subjecting it to a modified, basic threat analysis accentuated the findings of Mobjörk et al. and Dellmuth et al., discussed earlier, about the incoherent nature of climate-security conception. However, it was found that the incoherence is most significant at the strategic level: in the stance of nation-states, resource eagles, and in the impotence of governing bodies and international organizations against the hyperthreat’s modus operandi. This relates to fundamental philosophical stances or deep framing around threat, who defines it, analyses the threat, and structures threat response.
When it comes to CEC, modern people lack a concept of threat and lack language to articulate it, but they also may face societal taboos and difficult affective impacts of confronting wrongdoing. It is far easier to contemplate threat as being far away, or as some form of “other” rather than see it as people within one’s own social sphere.
Emblematized by the incapacity to determine the causes of the Iraq War or identify actors involved in harmful resource exploitation, much of the information needed to properly understand CEC hyperthreat enablers and dimensions is inaccessible.96 Further, the language and concepts and institutional structures that might allow such analysis are not well developed. This means that structural and conceptual framing factors limit accurate threat conception and may also lead to failure to identify synergistic opportunities.
The research was focused on understanding barriers to threat perception at the deep-framing level, and it concludes that these barriers remain significant. To reflect on the importance of this issue, deep frames influence which worldview becomes the dominant narrative, whereby it obtains power—the capacity to influence laws or funding decisions, for example. Yet, deep framing is also connected to truth and survival. Over time, the more accurate a frame is in depicting a complex and changing reality—and thereby proving its utility—the more trusted and accepted it becomes.
Deep frames or embodied understanding is complex, but at one level it can be understood as an attempt to match cognitive “software” with an unfolding and hard to decipher reality: it is the quest for perception and understanding to match the “truth” that best helps humanity survive a hazardous existence. Although humanity and planetary security depends on as accurate and truthful interpretation of threat as is possible (which allows the best chance of an effective response), achieving accurate perception can be thwarted by multiple actors who wish to distort threat narratives for their own agenda.
Nonetheless, as an independently conducted analytical activity, framing CEC as a hyperthreat provided a useful conceptual hinge that allowed new questions to be raised and new explorations to be undertaken. A grim finding was that the full threat spectrum has likely been underestimated, yet a hyper-level perspective also found that humanity has significant latent capacity. With many human structures, systems, and ideologies teetering, there is an opportunity for metamorphosis—for change to be orchestrated so that it aligns with an ambitious approach to a safe Earth pathway.97
Conclusion
Overall, this research project found that military methods did tangibly aid analysis of the CEC problem, however, what was more constructive was the fusion of these methods and concepts with other disciplines and emerging new philosophical constructs. Of high utility was the integrative strengths of analyzing the hyperthreat in the context of other security and military threats and bringing economic actors into the threat analysis process in a transparent way.
The research found that the danger and difficulty of the problem is immense and unlikely to be resolved without a substantial shift in the stance of nation-states and the international relations and security sector. Worse, the current trajectory involving increased global preparations for warfare and conflict could derail the chance to achieve a safe climate. It also found vast potential—an unexplored intellectual landscape abundant with new possibilities. A pathway does exist to reach safe Earth. It rests on two things: the pivot of state tribes’ and civilians’ mobilization.
This exploratory research informs the discussion about what an effective climate emergency response might look like. The hyperthreat and entangled security notions may offer some additional explanatory power and potentially a compelling new narrative that is accessible to the wider community. In terms of climate-security discourse, the research contributes to the wider discussion about how such issues are best conceptualized and translated into practice.
Considering the international relations, defense, and military sector, this research can help orient philosophical assumptions in a way that is attuned to the twenty-first century. In the era of CEC, this sector could be more than a bystander; the cleaner of hyperthreat mess; or an unwitting accomplice to the hyperthreat. Instead, there is an opportunity for significant realignment—for the sector to become an enabler of a global hyper-response while remaining aligned with its raison d’être of protecting its respective populations and ecological home base. The IPCC's latest report underscores the urgency of the situation:
The cumulative scientific evidence is unequivocal: climate change is a threat to human well-being and planetary health. Any further delay in concerted anticipatory global action on adaptation and mitigation will miss a brief and rapidly closing window of opportunity to secure a livable and sustainable future for all. (very high confidence).98
Endnotes
- Joelle Gergis, “We Are Seeing the Very Worst of Our Scientific Predictions Come to Pass in These Bushfires,” Guardian (Australia), 2 January 2020.
- “Boe Declaration on Regional Security,” Pacific Islands Forum, 2018; and “World Risks ‘Collapse of Everything’ without Strong Climate Action, Attenborough Warns Security Council,” UN News, 23 February 2021.
- Exec. Order 14008: Tackling the Climate Crisis at Home and Abroad (27 January 2021).
- For more detail on deep frames, see the glossary.
- George Lakoff, “Why It Matters How We Frame the Environment,” Environmental Communication 4, no. 1 (2014): 70–81, https://doi.org/10.1080/17524030903529749.
- E. G. Boulton, “An Introduction to PLAN E: Grand Strategy for the Twenty-First-Century Era of Entangled Security and Hyperthreats,” Expeditions with MCUP (2022).
- Timothy Morton, Hyperobjects: Philosophy and Ecology after the End of the World (Minneapolis: University of Minnesota Press, 2013); and Elizabeth Boulton, “Climate Change as a ‘Hyperobject’: A Critical Review of Timothy Morton’s Reframing Narrative,” WIREs Climate Change 7, no. 5 (September/October 2016): 176, https://doi.org/10.1002/wcc.410.
- Morton, Hyperobjects Philosophy and Ecology after the End of the World, 164.
- See glossary and the Expeditions article on PLAN E, which provides more theoretical background on both the hyperobject and hyperthreat concepts. The full definition also describes the hyperthreat’s enablers, as follows: the hyperthreat is powered and energized by three key enablers; its invisibility, its ability to evade all existing human threat-response mechanisms, and by human hesitancy––the slower humans are to act, the stronger it becomes. Elizabeth G. Boulton, “Climate Change as a Hyperthreat,” in Australian Contributions to Strategic and Military Geography, ed. Stuart Pearson, Jane L. Holloway, and Richard Thackway (Cham, Switzerland: Springer International Publishing, 2018).
- Eric Paglia, “The Socio-scientific Construction of Global Climate Crisis,” Geopolitics 23, no. 1 (2018): https://doi.org/10.1080/14650045.2017.1328407.
- Rob Nixon, Slow Violence and the Environmentalism of the Poor (Cambridge, MA: Harvard University Press, 2011).
- Pope Francis, Encyclical Letter: Laudato Si’ of the Holy Father Francis on Care for Our Common Home (Vatican City: Catholic Church, 2015).
- Nicholas Fotion, War & Ethics: A New Just War Theory (London: Continuum International Publishing Group, 2007). For a more detailed discussion, see the glossary and the Expeditions article; and “Climate Change as a Hyperthreat,” YouTube video, 7 September 2020, 3:47 min.
- Thierry Balzacq, Peter Dombrowski, and Simon Reich, “Is Grand Strategy a Research Program?: A Review Essay,” Security Studies 28, no. 1 (2019): 59, https://doi.org/10.1080/09636412.2018.1508631; and Basil Henry Liddell Hart, The Decisive Wars of History: A Study in Strategy (London: G. Bell & Sons, 1929).
- Nina Silove, “Beyond the Buzzword: The Three Meanings of ‘Grand Strategy’,” Security Studies 27, no. 1 (2018), https://doi.org/10.1080/09636412.2017.1360073.
- Peter Layton, Grand Strategy (Columbia, SC: Layton, 2018).
- “War is a mere continuation of policy by other means . . . not merely a political act, but also a real political instrument, a continuation of political commerce, a carrying out of the same by other means.” Carl Clausewitz, On War, ed. and trans. Anatol Rapoport (London: Penguin Books, 1968), 119.
- “Citizens’ Assemblies,” Extinction Rebellion, accessed 4 March 2022; and George Monbiot, “Rewilding Politics,” Monbiot.com, 23 December 2019.
- Our Global Neighbourhood: The Report of the Commission on Global Governance (New York: Commission on Global Governance, United Nations, 1995).
- Boulton, “Climate Change as a Hyperthreat.”
- Maria Julia Trombetta, “Environmental Security and Climate Change: Analysing the Discourse,” Cambridge Review of International Affairs 21, no. 4 (2008), https://doi.org/10.1080/09557570802452920.
- Joshua W. Busby, “Who Cares about the Weather?: Climate Change and U.S. National Security,” Security Studies 17, no. 3 (2008), https://doi.org/10.1080/096364 10802319529.
- Úrsula Oswald Spring, “A HUGE Gender Security Approach: Towards Human, Gender, and Environmental Security,” in Facing Global Environmental Change: Environmental, Human, Energy, Food, Health and Water Security Concepts, ed. Hans Günter Brauch et al. (Heildelberg, Germany: Springer Verlag, 2009); and Matt McDonald, Ecological Security: Climate Change and the Construction of Security (Cambridge, UK: Cambridge University Press, 2021), https://doi.org/10.1017/9781009024495.
- Toby Ord, The Precipice: Existential Risk and the Future of Humanity (New York: Hachette Books, 2020); Pablo Servigne and Raphaël Stevens, How Everything Can Collapse: A Manual for Our Times, trans. Andrew Brown (Hoboken, NJ: John Wiley & Sons, 2020); S. J. Beard et al., “Assessing Climate Change’s Contribution to Global Catastrophic Risk,” Futures, no. 127 (March 2021), https://doi.org/10.1016/j.futures.2020.102673; C. E. Richards, R. C. Lupton, and J. M. Allwood, “Re-framing the Threat of Global Warming: An Empirical Causal Loop Diagram of Climate Change, Food Insecurity and Societal Collapse,” Climatic Change 164, no. 3 (2021), https://doi.org/10.1007/s10584-021-02957-w; and Nathan Alexander Sears, “International Politics in the Age of Existential Threats,” Journal of Global Security Studies 6, no. 3 (2020), https://doi.org/10.1093/jogss/ogaa027.
- Malin Mobjörk et al., Climate-Related Security Risks: Towards an Integrated Approach (Solna, Sweden: Stockholm International Peace Research Institute, 2016).
- Lisa M. Dellmuth et al., “Intergovernmental Organizations and Climate Security: Advancing the Research Agenda,” WIREs Climate Change 9, no. 1 (January/February 2018), https://doi.org/10.1002/wcc.496.
- Joshua W. Busby, “Beyond Internal Conflict: The Emergent Practice of Climate Security,” Journal of Peace Research 58, no. 1 (2021), https://doi.org/10.1177/00223433 20971019.
- Sherilyn MacGregor and Nicole Seymour, eds., “Men and Nature: Hegemonic Masculinities and Environmental Change,” RCC Perspectives: Transformations in Environment and Society, no. 4 (2017), https://doi.org/10.5282/rcc/7977; Seema Arora-Jonsson, “Virtue and Vulnerability: Discourses on Women, Gender and Climate Change,” Global Environmental Change 21, no. 2 (May 2011), https://doi.org/10.1016/j.gloenvcha.2011.01.005; Janet K. Swim et al., “Gendered Discourse about Climate Change Policies,” Global Environmental Change, no. 48 (2018), https://doi.org/10.1016/j.gloenvcha.2017.12.005; and Nathan J. Cook, Tara Grillos, and Krister P. Andersson, “Gender Quotas Increase the Equality and Effectiveness of Climate Policy Interventions,” Nature Climate Change 9, no. 4 (2019), https://doi.org/10.1038/s41558-019-0438-4. See, for example, work by J. Ann Tickner, Gender in International Relations: Feminist Perspectives on Achieving Global Security (New York: Columbia University Press, 1992); Valerie M. Hudson et al., “The Heart of the Matter: The Security of Women and the Security of States,” International Security 33, no. 3 (2009); Jennifer Heeg Maruska, “When Are States Hypermasculine?,” in Gender and International Security: Feminist Perspectives, ed. Laura Sjoberg (Oxon, UK: Routledge, 2009); Annick T. R. Wibben, Researching War: Feminist Methods, Ethics and Politics (Abingdon-on-Thames, UK: Routledge, 2016); and Cara Daggett, “Petro-masculinity: Fossil Fuels and Authoritarian Desire,” Millennium 47, no. 1 (2018), https://doi.org/10.1177/0305829818775817.
- Paglia, “The Socio-scientific Construction of Global Climate Crisis.”
- Nick Bostrom, “Existential Risk Prevention As Global Priority,” Global Policy 4, no. 1 (2013), https://doi.org/10.1111/1758-5899.12002.
- The UN Security Council and Climate Change (New York: United Nations, 2021).
- Jochen Hinkel et al., “Transformative Narratives for Climate Action,” Climatic Change 160, no. 4 (2020), https://doi.org/10.1007/s10584-020-02761-y.
- Nick Mabey, “Security Trends and Threat Misperceptions,” in Britain and Security, ed. Paul Cornish (London: Smith Institute, 2007).
- Anthony Burke et al., “Planet Politics: A Manifesto from the End of IR,” Millennium 44, no. 3 (2016), https://doi.org/10.1177/0305829816636674.
- Simon Dalby, “National Security in a Rapidly Changing World,” Balsillie Papers 3, no. 3 (2020).
- “Safe Earth”—see glossary. In brief, it refers to avoiding dangerous climate change and ecological collapse, or the exceedance of scientifically defined planetary boundaries. It also generally encapsulates safety and peace of all forms. Johan Rockstrom et al., “A Safe Operating Space for Humanity,” Nature 461, no. 7263 (2009), http://dx.doi.org/10.1038/461472a.
- In general, harm-doing refers to actions that maim, damage, destroy, hurt, kill, or lead to such outcomes, across planetary, human, and state security spheres. Examples of harm-doing include actions that hasten ecological damage or global warming; for example, putting toxins in a river or undermining greenhouse gas (GHG) reduction policies.
- Joint Military Appreciation Process, Australian Defence Force Procedures 5.0.1, 2d ed. (Canberra, Australia: Department of Defence, 2019); Stefan J. Banach and Alex Ryan, “The Art of Design: A Design Methodology,” Military Review 99, no. 2 (March–April 2009). Center of gravity (COG) analysis seeks to identify the key factor that provides a force its power or ability to achieve its objectives. COG understanding drew on work from Aaron P. Jackson and Australian Defence Force doctrine. Aaron P. Jackson, “Center of Gravity Analysis ‘Down Under’: The Australian Defence Force’s New Approach,” Joint Force Quarterly, no. 84 (2017); and Joint Military Appreciation Process.
- Boulton, “Climate Change as a ‘Hyperobject’.”
- Real-options analysis is a method for decision making in environments of deep uncertainty, which involves actively identifying outlier possibilities. It won the 1997 Nobel Prize for Economics. Traditional risk planning estimated investment outcomes by drawing on known trajectories, while eliminating outlier possibilities. Real-options analysis takes the opposite approach; it “seeks out risky situations.” This keeps decision options and pathways open, such that if there were large fluctuations, choices that may have initially seemed unviable may become newly viable, and even lucrative. It is now applied across many disciplinary fields, including climate and environmental risk. Fischer Black and Myron Scholes, “The Pricing of Options and Corporate Liabilities,” Journal of Political Economy 81, no. 3 (May–June 1973), https://doi.org/10.1086/260062; Robert C. Merton, “Theory of Rational Option Pricing,” Bell Journal of Economics and Management Science 4, no. 1 (Spring 1973); and Joost Buurman and Vladan Babovic, “Adaptation Pathways and Real Options Analysis: An Approach to Deep Uncertainty in Climate Change Adaptation Policies,” Policy and Society 35, no. 2 (2016), https://doi.org/10.1016/j.polsoc.2016.05.002.
- Boulton, “Climate Change as a ‘Hyperobject’ ”; and Boulton, “Climate Change as a Hyperthreat.”
- Karen Barad, Meeting the Universe Halfway: Quantum Physics and the Entanglement of Matter and Meaning (Durham, NC: Duke University Press, 2007).
- Distinct from “interaction,” which describes the idea of two distinct, separately formed identities meeting, “intra-action” is the idea that both entities are partly formed through their ongoing interaction with each other. Barad, Meeting the Universe Halfway, 35.
- Niels Bohr, Essays 1958–1962 on Atomic Physics and Human Knowledge (Woodbridge, CT: Ox Bow Press, 1963).
- Barad, Meeting the Universe Halfway, 183.
- “Continuous discourse” is explained further in the glossary, and the concept forms part of the “entangled security” conceptual compass, shown in figure 4.
- See glossary. Ethico refers to ethics. Onto refers to ontology—a branch of philosophy that considers the nature of “being” and existence. Epistemology is a branch of philosophy that considers how human’s know things. Barad draws on quantum physics to argue that these three dimensions of philosophy are interdependent and thus should not be considered in isolation.
- Matter matters refers to a conceptual idea. See glossary and figure 4 for explanation. Timothy Morton also uses the term “co-agency.” Morton, Hyperobjects.
- Discussed, for example, by Nathan P. Freier et al., At Our Own Peril: DoD Risk Asessment in a Post-Primacy World (Carlisle, PA: U.S. Army War College Press, 2017); and Thitinan Pongsudhirak, “Maintaining What’s Left of Rules-Based Order,” Bangkok Post (Thailand), 20 July 2018.
- Freedom in the World, 2021: Democracy under Siege (Washington, DC: Freedom House, 2021).
- Susan Park, International Organisations and Global Problems: Theories and Explanations (Cambridge, UK: Cambridge University Press, 2018), https://doi.org/10.1017/9781139924788; and Naghmeh Nasiritousi and Soetkin Verhaegen, “Disentangling Legitimacy: Comparing S Assessments of Five Key Climate and Energy Governance Institutions,” in Governing the Climate-Energy Nexus: Institutional Complexity and Its Challenges to Effectiveness and Legitimacy, ed. Fariborz Zelli et al. (Cambridge, UK: Cambridge University Press, 2020), https://doi.org/10.1017/9781108676397.
- Two books that discuss hate crimes: Sue Lloyd-Roberts, The War on Women: And the Brave Ones Who Fight Back (London: Simon and Schuster, 2016); and Michael Kimmel, Healing from Hate (Oakland: University of California Press, 2018).
- Carol Cohn and Claire Duncanson, “Women, Peace and Security in a Changing Climate,” International Feminist Journal of Politics 22, no. 5 (2020), https://doi.org/10.1080/14616742.2020.1843364.
- Facundo Alvaredo et al., “The Elephant Curve of Global Inequality and Growth,” AEP Papers and Proceedings, no. 108 (2018), https://doi.org/10.1257/pandp.20181073; and Daniel S. Hoadley and Nathan J. Lucas, Artificial Intelligence and National Security (Washington, DC: Congressional Research Service, 2018).
- The Sustainable Development Goals Report, 2018 (New York: Development Data and Outreach Branch, United Nations Statistics Division, 2018).
- The Sustainable Development Goals Report, 2021 (New York: United Nations, 2021).
- Rosanna E. Guadagno and Karen Guttieri, “Fake News and Information Warfare: An Examination of the Political and Psychological Processes from the Digital Sphere to the Real World,” in Research Anthology on Fake News, Political Warfare, and Combatting the Spread of Misinformation (Hershey, PA: IGI Global, 2021), https://doi.org/10.4018/978-1-5225-8535-0.ch011.
- Eiríkur Bergmann, “Populism and the Politics of Misinformation,” Safundi 21, no. 3 (2020), https://doi.org/10.1080/17533171.2020.1783086. See, for example, Florian Hartleb, “Right-Wing Terrorism: Still an Underestimated Threat,” in Lone Wolves: The New Terrorism of Right-Wing Single Actors (Chatham, Switzerland: Springer, 2020), https://doi.org/10.1007/978-3-030-36153-2_1; and Ziya Öniş and Mustafa Kutlay, “The Global Political Economy of Right-wing Populism: Deconstructing the Paradox,” International Spectator 55, no. 2 (2020), https://doi.org/10.1080/03932729.2020.1731168.
- Diego Lopes da Silva, Nan Tian, and Alexandra Marksteiner, Trends in World Military Expenditure (Solna, Sweden: Stockholm International Peace Research Institute, 2020), https://doi.org/10.55163/JTFI7245.
- J. J. Messner et al., 2018 Fragile States Index: Annual Report (Washington, DC: Fund for Peace, 2018); David Kilcullen, “Geographies of Irregular Warfare,” in Australian Contributions to Strategic and Military Geography, ed. Stuart Pearson, Jane L. Holloway, and Richard Thackway (Cham, Switzerland: Springer International Publishing, 2018); and Graham Allison, Destined for War: Can America and China Escape Thucydides’s Trap? (Boston, MA: Houghton Mifflin Harcourt, 2017). See, for example, reflections by Stephen Blank, “Russia’s Vostok-2018: A Rehearsal for Global War?,” Interpreter, 4 September 2018; and Hal Brands, “New Threat to the US: the Axis of Autocracy,” Bloomberg Opinion, 19 April 2018.
- John Keane, “Enter the Dragon: Decoding the New Chinese Empire,” Australian Foreign Affairs, no. 11 (February 2021). See the glossary for more on “Galaxy Empire.”
- W. N. Adger et al., “Human Security,” in Climate Change 2014: Impacts, Adaptation, and Vulnerability, pt. A, Global and Sectoral Aspects: Contribution of Working Group II to the Fifth Assessment Report of the Intergovernmental Panel on Climate Change, ed. C. B. Field et al. (Cambridge, UK: Cambridge University Press, 2014), chap. 12, table 12-4, 778.
- See glossary. Tribal discourse is a new way of grouping and analyzing human activity in relation to the hyperthreat. It represents a nonhuman-centered approach in that the hyperthreat is centered, and human activity is understood in relation to the hyperthreat. It breaks from modern ways of thinking, such as using nation-state categories, to offer a new analytical lens.
- See figure 6. Earth protectors includes park rangers, environmental activists, animal rescue, and frontline environmental protection agencies. These are people actively protecting the nonhuman from ecocide, violence, and harm.
- Christopher Nellemann et al., The Rise of Environmental Crime: A Growing Threat to Natural Resources, Peace, Development and Security (Nairobi, Kenya: United Nations Environment Programme, 2016), 39.
- Channing May, Transnational Crime and the Developing World (Washington, DC: Global Financial Integity, 2017), xi; and The State of Knowledge of Crimes that Have Serious Impacts on the Environment (Nairobi, Kenya: United Nations Environment Programme 2018), ix.
- Elizabeth Lunstrum, “Green Militarization: Anti-Poaching Efforts and the Spatial Contours of Kruger National Park,” Annals of the Association of American Geographers 104, no. 4 (2014), https://doi.org/10.1080/00045608.2014.912545.
- Christian Nellemann et al., eds., The Environmental Crime Crisis: Threats to Sustainable Development from Illegal Exploitation and Trade in Wildlife and Forest Resources (Nairobi, Kenya: United Nations Environment Programme, 2014).
- Goemeone Emmanuel Judah Mogomotsi and Patricia Kefilwe Madigele, “Live by the Gun, Die by the Gun: Botswana’s ‘Shoot-to-Kill’ Policy as an Anti-Poaching Strategy,” South African Crime Quarterly, no. 60 (June 2017), http://dx.doi.org/10.17159/2413-3108/2017/v0n60a1787.
- See work by Lukas Rüttinger et al., A New Climate for Peace Taking Action on Climate and Fragility Risks (Paris: European Union Institute for Security Studies, 2015); and Carlos Alberto Cruz, Improving Security of United Nations Peacekeepers: We Need to Change the Way We Are Doing Business (New York: United Nations, 2017).
- David Brown et al., “Modern Slavery, Environmental Degradation and Climate Change: Fisheries, Field, Forests and Factories,” Environment and Planning E: Nature and Space 4, no. 2 (2021), https://doi.org/10.1177/2514848619887156.
- Michael Barnett, Empire of Humanity: A History of Humanitarianism (Ithaca, NY: Cornell University Press, 2011).
- Katharina Nett and Lukas Rüttinger, Insurgency, Terrorism and Organised Crime in a Warming Climate—Analysing the Links Between Climate Change and Non-State Armed Groups (Berlin, Germany: Adelphi, 2016), 55.
- Tobias von Lossow, “The Rebirth of Water as a Weapon: IS in Syria and Iraq,” International Spectator 51, no. 3 (2016), https://doi.org/10.1080/03932729.2016.1213063; and Jamie Hansen-Lewis and Jacob N. Shapiro, “Understanding the Daesh Economy,” Perspectives on Terrorism 9, no. 4 (2015).
- Robert Goralski and Russell W. Freeburg, Oil and War: How the Deadly Struggle for Fuel in WWII Meant Victory or Defeat (Quantico, VA: Marine Corps University Press, 2021 reprint; 1987).
- Stephen A. Marglin and Juliet B. Schor, The Golden Age of Capitalism: Reinterpreting the Postwar Experience (Oxford, UK: Oxford University Press, 1990), https://doi.org/10.1093/acprof:oso/9780198287414.001.0001; and Paul Warde, Libby Robin, and Sverker Sörlin, The Environment: A History of the Idea (Baltimore, MD: Johns Hopkins University Press, 2018).
- Donella H. Meadows, Jørgen Randers, and William W. Behrens, The Limits to Growth: A Report to the Club of Rome on the Predicament of Mankind (New York: Universe Books, 1972).
- Doug Stokes, “Blood for Oil?: Global Capital, Counter-insurgency and the Dual Logic of American Energy Security,” Review of International Studies 33, no. 2 (April 2007), https://doi.org/10.1017/S0260210507007498.
- Neil Smith, “After the American Lebensraum ‘Empire,’ Empire, and Globalization,” Interventions 5, no. 2 (2003), https://doi.org/10.1080/1369801031000112987; and John Morrissey, The Long War: CENTCOM, Grand Strategy, and Global Security (Athens: University of Georgia Press, 2017).
- Stokes, “Blood for Oil?”
- See, for example, “The Revolution of Thomas Sankara,” African Agenda, 3 October 2017; Mary Kaldor, Terry Lynn Karl, and Yahia Said, eds., Oil Wars (London: Pluto Press, 2007); Michael T. Klare, The Race for What’s Left: The Global Scramble for the World’s Last Resources (New York: Macmillan, 2012); and John Perkins, The New Confessions of an Economic Hit Man (Oakland, CA: Berrett-Koehler Publishers, 2016).
- Sir John Chilcot, The Report of the Iraq Inquiry: Executive Summary (London, UK: House of Commons, 2016); Jeff D. Colgan, “Oil and Security: The Necessity of Political Economy,” Journal of Global Security Studies 6, no. 1 (March 2021), https://doi.org/10.1093/jogss/ogaa008; and Jeff D. Colgan, “Fueling the Fire: Pathways from Oil to War,” International Security 38, no. 2 (Fall 2013), https://doi.org/10.1162/ISEC_a_00135.
- “Overexposed—How the IPCC’s 1.5 Degree Report Demonstrates the Eisks of Overinvestment in Oil and Gas,” Global Witness, 23 April 2019.
- Tran Truong Thuy, John B. Welfield, and Le Thuy Trang, eds., Building a Normative Order in the South China Sea: Evolving Disputes, Expanding Options (Cheltenham, UK: Edward Elgar Publishing, 2019).
- Hui Zhong and Michael White, “South China Sea: Its Importance for Shipping, Trade, Energy and Fisheries,” Asia-Pacific Journal of Ocean Law and Policy 2, no. 1 (2017): 17–19, https://doi.org/https://doi.org/10.1163/24519391-00201003.
- See the glossary. The term dual-logic was first used by Doug Stokes in “Blood for Oil?”
- Report of the World Commission on Environment and Development: Our Common Future (Oxford, UK: Oxford University Press, 1987); J. T. Houghton, G. J. Jenkins, and J. J. Ephraums, Climate Change: The IPCC Scientific Assessment (Cambridge, UK: Cambridge University Press, 1990); Our Global Neighbourhood: The Report of the Commission on Global Governance (Oxford, UK: Oxford University Press, 1995).
- A selection of research on climate denialism includes Geoffrey Supran and Naomi Oreskes, “Assessing ExxonMobil’s Climate Change Communications (1977–2014),” Environmental Research Letters 12, no. 8 (2017); Naomi Oreskes and Erik M. Conway, Merchants of Doubt: How a Handful of Scientists Obscured the Truth on Issues from Tobacco Smoke to Climate Change (New York: Bloomsbury, 2010); “Big Oil’s Real Agenda on Climate Change,” InfluenceMap, accessed 8 March 2023; and Robert J. Brulle, “The Climate Lobby: A Sectoral Analysis of Lobbying Spending on Climate Change in the USA, 2000 to 2016,” Climatic Change 149, no. 3 (2018), https://doi.org/10.1007/s10584-018-2241-z.
- See the glossary for more explanation on a “hothouse Earth” scenario. In brief, it is also referred to as a greenhouse Earth state, and a hothouse Earth state is expected to involve sea-level rise of 10–60 meters, and Earth’s mean surface temperature being four to five degrees above preindustrial levels. See data on the Middle Miocene epoch, in supporting documents to Will Steffen et al., “Trajectories of the Earth System in the Anthropocene,” Proceedings of the National Academy of Sciences 115, no. 33 (2018), https://doi.org/10.1073/pnas.1810141115.
- Hannah Arendt, Eichmann in Jerusalem: A Report on the Banality of Evil (New York: Penguin, 1963).
- Stanley Milgram, “Behavioral Study of Obedience,” Journal of Abnormal and Social Psychology 67, no. 4 (1963), https://doi.org/10.1037/h0040525.
- “The Duluth Model,” theduluthmodel.org, accessed 7 October 2018; and Ellen Pence and Michael Paymar, Education Groups for Men Who Batter: The Duluth Model (New York: Springer Publishing Company, 1993).
- Boulton, “An Introduction to PLAN E.”
- “Our Ocean, Our Future, Our Responsibility (Zero Draft)” (UN Ocean Conference, Lisbon, Portugal, 27 June–1 July 2022).
- IPCC, Climate Change 2022: Impacts, Adaptation, and Vulnerability (Cambridge, UK: Cambridge University Press, 2022), 34.
- Chilcot, The Report of the Iraq Inquiry. An example of the difficulty in identifying “who” conducts resource extraction activity is seen in the case of copper mining in Africa. Equity in Extractives: Stewarding Africa’s Natural Resources for All: Africa Progress Report 2013 (Geneva, Switzerland: United Nations, 2013), 56–57.
- See the glossary for detail. Safe Earth refers to avoiding dangerous climate change, (maintaining Earth’s mean temperature to 1.5 degrees above preindustrial levels), but also staying within other planetary boundaries outlined by Johan Rockström et al., such as limiting chemical pollution, ozone depletion, and biodiversity loss. The term safe Earth within PLAN E also refers to safety for all of Earth’s inhabitants, including the full range of human security concerns, from warfare, human trafficking, and sexual violence to food and water security among other issues encapsulated within the UN SDG. Johan Rockstrom et al., “A Safe Operating Space for Humanity,” Nature 461, no. 7263 (2009), http://dx.doi.org/10.1038/461472a.
- IPCC, Climate Change 2022, 35.